Being involved in microservice oriented and or container based application architecture usually implies having a lot of terminals with running processes during app development. Occasionally ports are blocked by a crashed service or port conflicts between docker desktop and local running daemons.
I always forget which commands to run on Mac OS to find out which ports are in use. For Linux it’s something like:
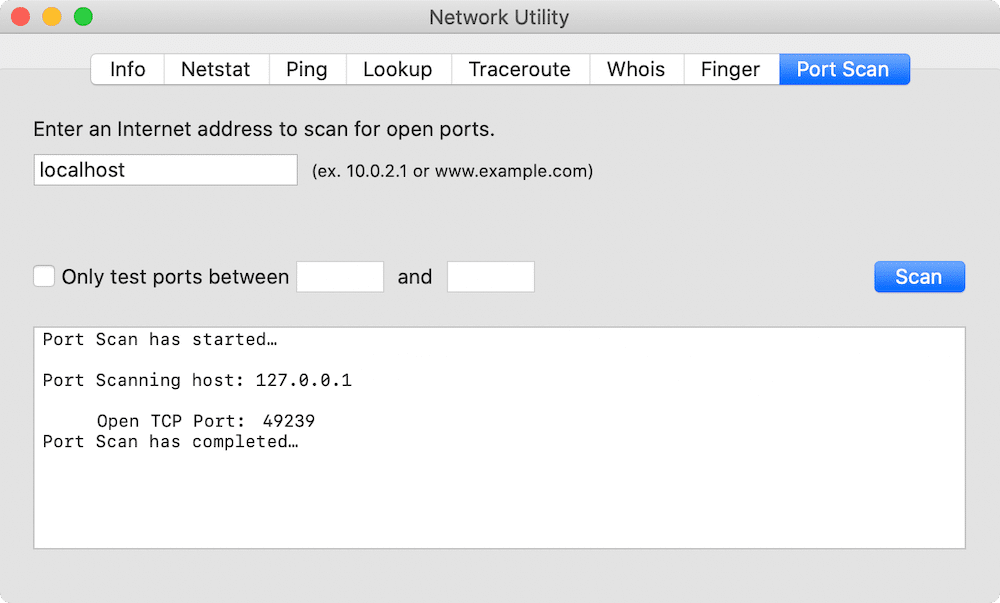
You could use the graphical port scanner, that’s available from the Mac Network Utility program, on 127.0.0.1 or
localhost to list the ports but that’s slow and it doesn’t show reliable info about the processes using it.
The weird thing is that netstat is actually installed but somehow the command line options differ subtly, like they
also do for dd and fdisk. The best readable way I could find:
Example Output
But lsof is faster, better sorted and includes the process names:
Example output:
Hope it helps me and/or others in the future when I need this info again 😎
Related Posts
Quick Links
Legal Stuff
